
AI for Cybersecurity: Enhancing Digital Defense 2024
http://AI for Cybersecurity: Enhancing Digital Defense 2024
Introduction
In today’s digital landscape, cybersecurity threats are evolving rapidly, necessitating more sophisticated defense mechanisms. AI plays a pivotal role in enhancing cybersecurity by leveraging powerful algorithms and data-driven techniques to predict, detect, and mitigate potential threats effectively. This blog will cover key applications and techniques used in AI for cybersecurity, focusing on intrusion detection, threat intelligence, and fraud detection.
Applications of AI in Cybersecurity

- Intrusion Detection Intrusion Detection Systems (IDS) utilize AI to monitor network traffic and detect suspicious activities. AI algorithms analyze data in real-time and identify anomalies that could indicate a security breach. This proactive approach helps in identifying threats before they escalate.Example Algorithm: Anomaly Detection Using Machine Learning AI-driven IDS often use anomaly detection techniques to distinguish normal behavior from potential threats. An anomaly detection model can be represented as:
// Pseudo-code for an anomaly detection model def detect_anomalies(data, threshold): for entry in data: score = calculate_anomaly_score(entry) if score > threshold: report_anomaly(entry) </pre>- Threat Intelligence AI enhances threat intelligence by analyzing vast amounts of data from different sources to identify patterns and predict potential security incidents. By correlating information, AI systems can assess risks and provide actionable insights for preemptive action.Predictive Analytics Formula Predictive models use historical data to forecast future threats. A basic predictive model can be mathematically represented as:htmlCopy code
<pre> y = β0 + β1x1 + β2x2 + ... + βnxn + ε </pre>Where:- yyy is the predicted output (e.g., probability of an attack),
- β0β0β0 is the intercept,
- β1,β2,…,βnβ1, β2, …, βnβ1,β2,…,βn are the coefficients for input features x1,x2,…,xnx1, x2, …, xnx1,x2,…,xn,
- εεε is the error term.
- Fraud Detection AI-driven fraud detection systems are adept at recognizing unusual patterns that could indicate fraudulent activities. By applying machine learning algorithms, these systems learn from historical fraud data and continuously adapt to new types of fraud.Example Code for Fraud Detection Using Anomaly Detection
// Python code to demonstrate fraud detection from sklearn.ensemble import IsolationForest # Load and prepare the dataset data = load_data('transaction_data.csv') model = IsolationForest(n_estimators=100, contamination=0.1) # Fit the model model.fit(data) # Predict anomalies (fraud cases) predictions = model.predict(data) anomalies = data[predictions == -1] print("Potential fraud cases detected:", len(anomalies)) </pre>
Techniques in AI for Cybersecurity
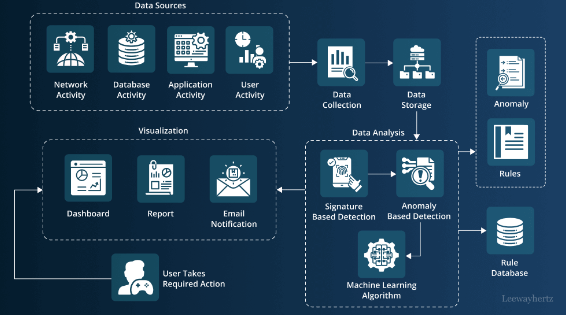
- Anomaly Detection Anomaly detection involves identifying data points that deviate significantly from the normal pattern. Techniques like statistical methods, clustering, and deep learning are employed for anomaly detection in cybersecurity.
- Predictive Analytics Predictive analytics utilizes data mining, statistics, and machine learning to predict future events. In cybersecurity, this technique helps forecast potential breaches and proactively fortify defenses.Example Visualization Code
<pre> // Code snippet to visualize prediction results import matplotlib.pyplot as plt # Example data x = range(len(actual_values)) plt.plot(x, actual_values, label='Actual') plt.plot(x, predicted_values, label='Predicted', linestyle='--') plt.xlabel('Time') plt.ylabel('Threat Level') plt.title('Predicted vs Actual Threat Levels') plt.legend() plt.show() </pre>
How Can We Leverage AI for Cybersecurity Advancements?
Implementing artificial intelligence in cyber security holds immense potential for addressing the complex challenges we face today. As the threat landscape starts to grow and devices become increasingly prevalent, AI and machine learning can play a vital role in combating cyberattacks by automating threat detection and response, surpassing traditional software-driven approaches.
However, cybersecurity presents unique hurdles that require innovative solutions:
- Expansive Attack Surface: Organizations deal with tens or hundreds of thousands of devices, each posing a potential vulnerability.
- Numerous Attack Vectors: Cyber threats emerge through various avenues, making monitoring and securing multiple entry points crucial.
- Scarce Security Professionals: A shortage of skilled security experts highlights the need for technology to augment their capabilities.
- Data Overload: The volume of data has exceeded human-scale processing, necessitating AI-powered systems to handle the massive influx of information effectively.
Benefits
Protecting data across hybrid cloud environments
AI tools can identify shadow data, monitor for abnormalities in data access and alert cybersecurity professionals about potential threats by malicious actors accessing the data or sensitive information—saving valuable time in detecting and remediating issues in real time.
Generating more accurate and prioritized threats
AI-powered risk analysis can produce incident summaries for high-fidelity alerts and automate incident responses, accelerating alert investigations and triage by an average of 55%. The AI technology also helps identify vulnerabilities across threat landscapes and defend against cybercriminals and cyber crime.
Balancing user access needs and security
AI models can help balance security with user experience by analyzing the risk of each login attempt and verifying users through behavioral data, simplifying access for verified users and reducing the cost of fraud by up to 90%. Also, AI systems help prevent phishing, malware and other malicious activities, ensuring a high security posture within security systems.
SolutionsIBM Threat Detection and Response Services (TDR)
How Cybersecurity Benefits from AI?
A self-learning AI-based cybersecurity posture management system proves indispensable in overcoming these challenges. By continuously and autonomously collecting data from an organization’s information systems, this system can analyze and correlate patterns across millions or billions of signals relevant to the enterprise’s attack surface.
This innovative approach provides enhanced intelligence to human teams across various cybersecurity domains, including:
- IT Asset Inventory: Achieving a comprehensive and accurate inventory of all devices, users, and applications with access to information systems while categorizing and assessing business criticality.
- Threat Exposure: Staying up to date with global and industry-specific threats, empowering organizations to prioritize security measures based on likelihood and potential impact.
- Controls Effectiveness: Assessing the impact and efficacy of existing security tools and processes to strengthen security posture.
- Breach Risk Prediction: Predicting vulnerability and potential breaches by considering IT asset inventory, threat exposure, and control effectiveness, enabling proactive resource allocation for mitigation.
- Incident Response: Providing contextual insights to prioritize and respond swiftly to security alerts, identify root causes, and improve incident management processes.
- Transparent solutions: Ensuring that AI recommendations and analyses are transparent and understandable, fostering collaboration and support from stakeholders at all levels of the organization, including end users, security operations, management, and auditors.
By harnessing the power of AI in cyber security, organizations can augment their cybersecurity capabilities, enhance their resilience against cyber threats, and enable effective communication and decision-making in the face of evolving risks.
The role of AI in cyber security has become essential in bolstering human efforts in information security. As the enterprise attack surface expands, AI aids in identifying and analyzing threats, reducing breach risk, and enhancing security posture. It excels in risk prioritization, malware detection, incident response guidance, and intrusion detection.
Conclusion
The use of AI in cybersecurity provides a robust framework for detecting and mitigating potential threats in real-time. Techniques like anomaly detection and predictive analytics enhance the ability to foresee and neutralize cyber threats, ensuring greater protection of digital assets. Leveraging these AI-driven methods equips cybersecurity teams with the tools necessary to stay ahead in the ever-evolving threat landscape.
By integrating AI into cybersecurity measures, organizations can not only react more swiftly to incidents but also strengthen their overall security posture to prevent future breaches.